Checking for Electrical Level Security Threats in FPGA Bitstreams
This website provides the code to our tools for checking FPGA bitstreams for potential circuits that are malicious on the electrical level (fault or side-channel attacks within the chip, from one region to another). This set of tools is currently implemented for Lattice iCE40, but could be adapted to other FPGAs as well, if enough tools and documentation on the bitstreams is available.
Summary of the topic, for details please refer to our publication [1] and respective citations inside that publication.
- Multi-tenant usage of FPGA fabric is a rising trend in the cloud and reconfigurable SoCs.
- Recent studies show that this trend also comes with new security vulnerabilities on the fundamental electrical level of the system.
- By maliciously re-using FPGA primitives, fault and side-channel attacks can even be performed through software, impacting the security of the entire system from the bottom up.
- We show the first attempt of countermeasures against these attacks, by analyzing FPGA bitstreams for malicious logic, basically implementing an "FPGA antivirus".
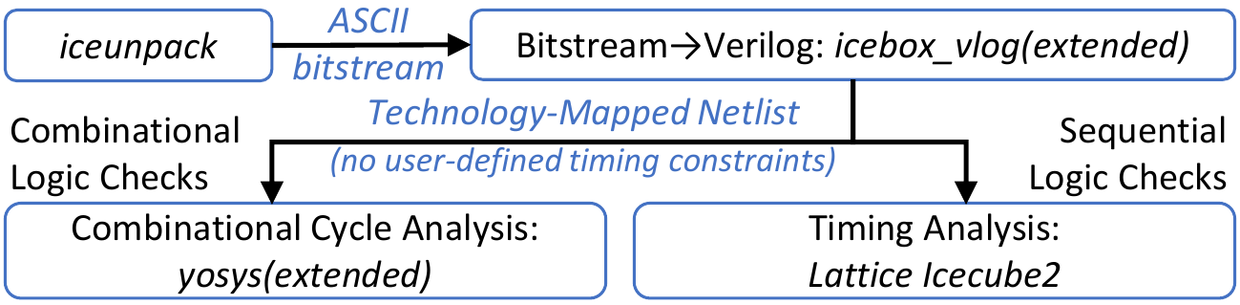
- We provide a way to check bitstreams for potentially malicious structures, by extending a combination of commercial and open-source tools.
The code package with respectively patched yosys and icestorm versions is available:
Dependencies for this package are:
- Python3 graph-tool
- Lattice icecube2 (tested with version 2017.08), added to PATH variable
- Tested in Ubuntu Linux 18.04 (bionic)
On any questions please contact either of:
If you are using this tool, please cite the following paper. Please also credit Clifford Wolf for yosys and icestorm:
[1] D. R. E. Gnad, S. Rapp, J. Krautter, M. B. Tahoori, "Checking for Electrical Level Security Threats in Bitstreams for Multi-Tenant FPGAs", International Conference on Field-Programmable Technology (FPT), 2018, Japan. [PDF]
