Software-based Fault and Power Side-Channel Attacks inside Multi-Tenant FPGAs
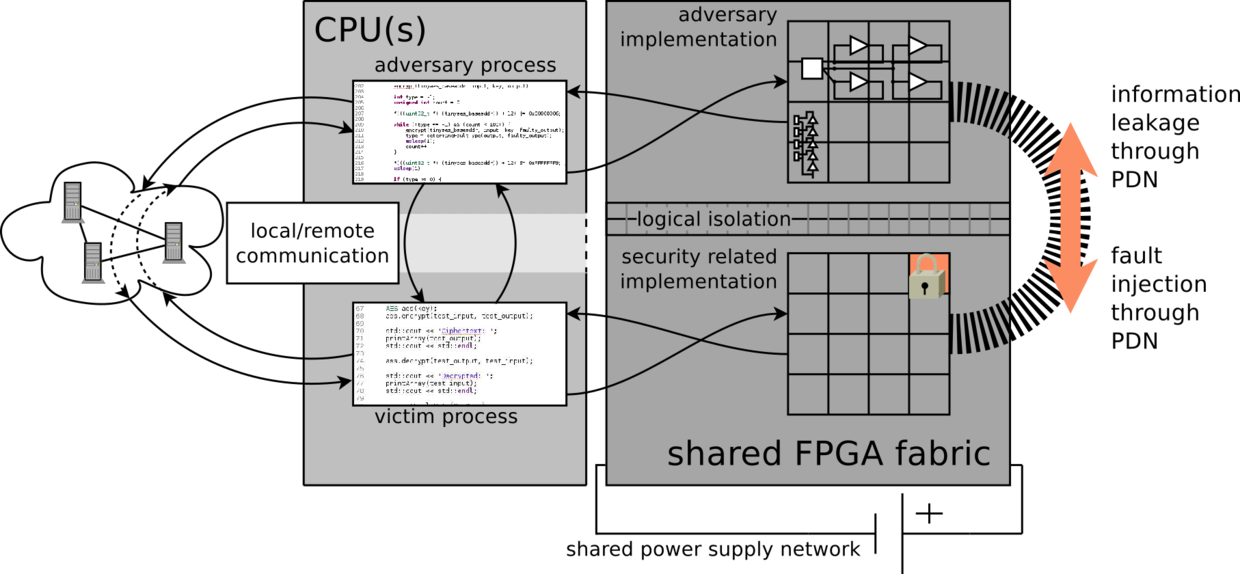
FPGAs are getting increasingly adopted as accelerators in clouds and data centers. In many of such emerging applications of FPGAs, multi-tenant usage of a single FPGA through virtualization is envisioned. This mandates the security and proper isolation at logical level. However, as shown recently, FPGA primitives can be re-used for attacks on the underlying electrical level. Previously, such attacks typically relied on expensive test and measurement equipment which mandated physical access to the system under attack. We could show that FPGA primitives can be re-used for sensors and fault injection on the electrical level, sufficient to remotely deploy power analysis side channel and fault analysis attacks, on Intel, Xilinx and Lattice FPGAs. The demo application you can download below, shows such attacks on a low-cost Lattice iCE40HX8K board.
In the compressed archive, you find four separate projects in total. Three of them contain the VHDL/Verilog source files to implement three variants of the described attacks on the Lattice iCE40HX8K breakout board. To build the FPGA projects, the free Lattice iCEcube2 software is required. iCEcube2 Project files are provided in the respective subfolders.
DFA
This FPGA application allows to deploy a fault attack on an AES encryption module to recover the secret key via Differential Fault Analysis (DFA). The faults are injected using a grid of ring oscillators, which is toggled with a specific frequency and duty-cycle. Attack parameters, plaintexts and ciphertexts are transferred via UART interface. The UART RTS signal controls the FPGA reset. For further details please see the source files of the project.
SCA
When deploying the SCA application on the iCE40HX8K, a side-channel attack (SCA) on the AES encryption module can be performed. A delay sensor made from FPGA primitives is used to estimate supply voltage, allowing to recover the secret AES key via Correlation Power Analysis (CPA). Again, the communication with the FPGA is established through the UART interface, where the FPGA expects a 16 byte plaintext and replies with a 16 byte ciphertext and a 280 byte trace. Each byte in the trace corresponds to a sensor measurement and can be used for CPA at that point. The RTS signal resets the FPGA.
DoS
To demonstrate a Denial-of-Service attack, the iCE40HX8K is filled up with ring oscillators and two testing modules that cause two LEDs on the board to blink synchronously every second. Sending a lowercase 's' on the UART interface to the FPGA, causes it to toggle the ring oscillators on and off with decreasing frequency and increasing duty-cycle for each frequency. The LEDs will not blink synchronously anymore and one of the blinking processes may crash completely, leaving the LED in a constant on or off state. At this point, the FPGA has to be reprogrammed to return to the initial state. Not all boards are equally vulnerable, a crash may not be possible on all iCE40HX8K breakout boards.
PC Graphical User Interface (GUI) Project
The fourth project is a Qt5 based host application, used for interaction with the FPGA. To build it, Qt5 including the QtCharts library and their respective development files are required. All preconfigured parameters match the parameters of the FPGA projects, except for the serial port name on your system. The host application has been tested on x86_64 Linux systems.
Needed Hardware
The demos only require the Lattice iCE40HX8K Breakout Board, and can be ported to platforms of other vendors as well, which we might add in the future. Please let us know if you are interested in other vendors.
Support, Licensing & Citing
If you encounter problems or have further questions, you may contact Jonas Krautter <jonas krautter ∂does-not-exist.kit edu> via e-mail.
This hardware demonstration was developed together with the Ruhr Universität Bochum and is released under the MIT open-source license. Please see the respective source file headers for details.
If you use this work in academic publications, please cite this combined work:
- J. Krautter, D. R. E. Gnad, F. Schellenberg, A. Moradi, M. B. Tahoori, "Software-based Fault and Power Side-Channel Attacks inside Multi-Tenant FPGAs", Demo Session, IEEE International Symposium on Hardware Oriented Security and Trust (HOST), 2019, USA.
This demo won the Third Place BEST Hardware Demo Award at HOST 2019.
For the specific attacks respectively, these can be cited:
- D. R. E. Gnad, F. Oboril, M. B. Tahoori, "Voltage Drop-based Fault Attacks on FPGAs using Valid Bitstreams", International Conference on Field-Programmable Logic and Applications (FPL), 2017, Belgium.
- F. Schellenberg, D. R. E. Gnad, A. Moradi, M. B. Tahoori, "An Inside Job: Remote Power Analysis Attacks on FPGAs", in proceedings of Design, Automation & Test in Europe (DATE), 2018, Germany.
- J. Krautter, D. R. E. Gnad, M. B. Tahoori, "FPGAhammer: Remote Voltage Fault Attacks on Shared FPGAs, suitable for DFA on AES", in IACR Transactions on Cryptographic Hardware and Embedded Systems (TCHES), 2018.
